In today's interconnected world, RemoteIoT VPC has become a cornerstone for organizations seeking to deploy secure and scalable Internet of Things (IoT) infrastructures. As the demand for remote IoT management grows, understanding RemoteIoT VPC is crucial for businesses looking to harness the full potential of IoT technology. This guide will delve deep into the concept, benefits, and implementation strategies of RemoteIoT VPC, ensuring you're equipped with the knowledge needed to make informed decisions.
As more devices come online, the need for robust network architecture becomes increasingly apparent. RemoteIoT VPC offers a solution by providing a secure virtual private cloud environment tailored specifically for IoT applications. This ensures that data transmission remains private and protected against unauthorized access, which is vital for industries handling sensitive information.
This article will explore the intricacies of RemoteIoT VPC, covering everything from its foundational principles to advanced deployment techniques. Whether you're a developer, IT professional, or business owner, this guide will provide actionable insights to help you optimize your IoT infrastructure.
Table of Contents
- What is RemoteIoT VPC?
- Importance of VPC for IoT
- Key Components of RemoteIoT VPC
- Benefits of Using RemoteIoT VPC
- Security Features of RemoteIoT VPC
- Deployment Strategies for RemoteIoT VPC
- Scaling and Management
- Common Challenges and Solutions
- Real-World Applications of RemoteIoT VPC
- Future Trends in RemoteIoT VPC
What is RemoteIoT VPC?
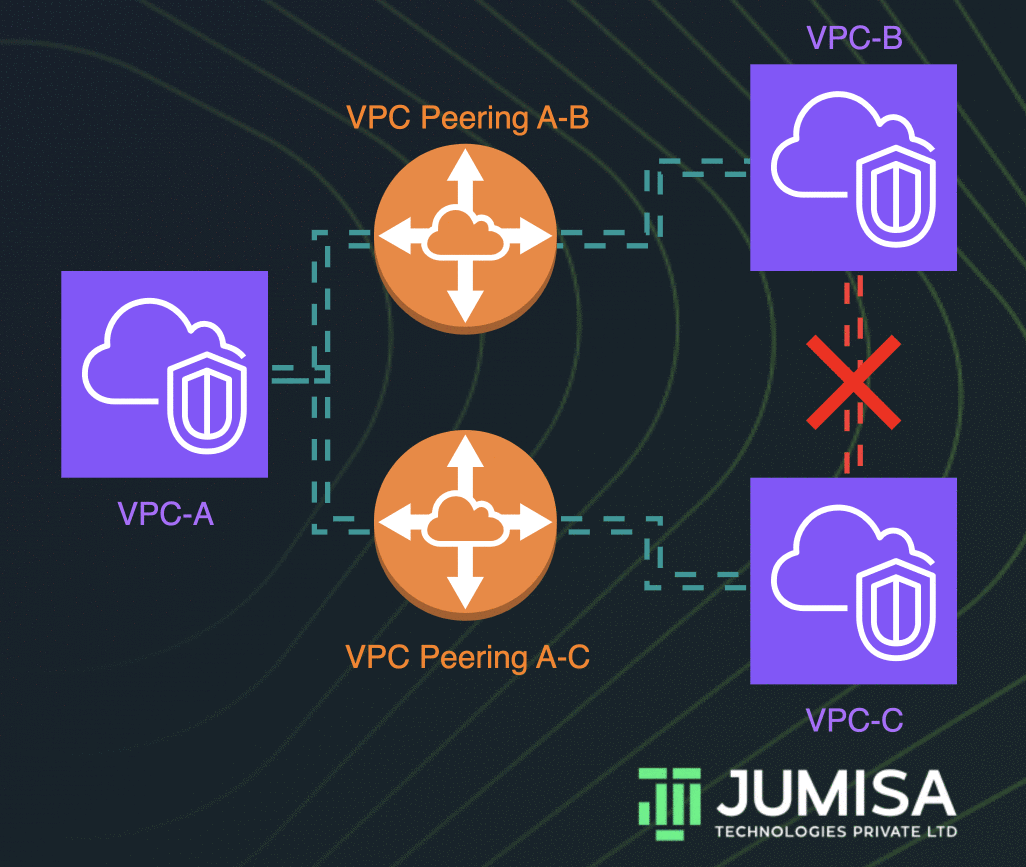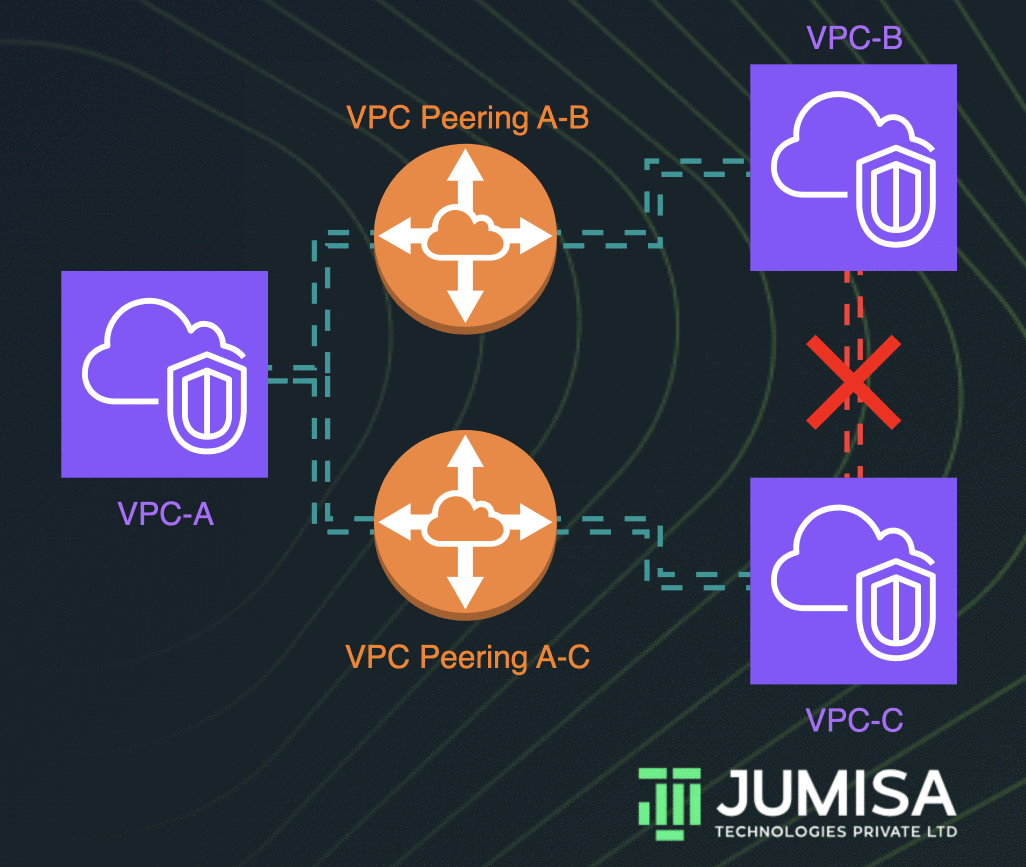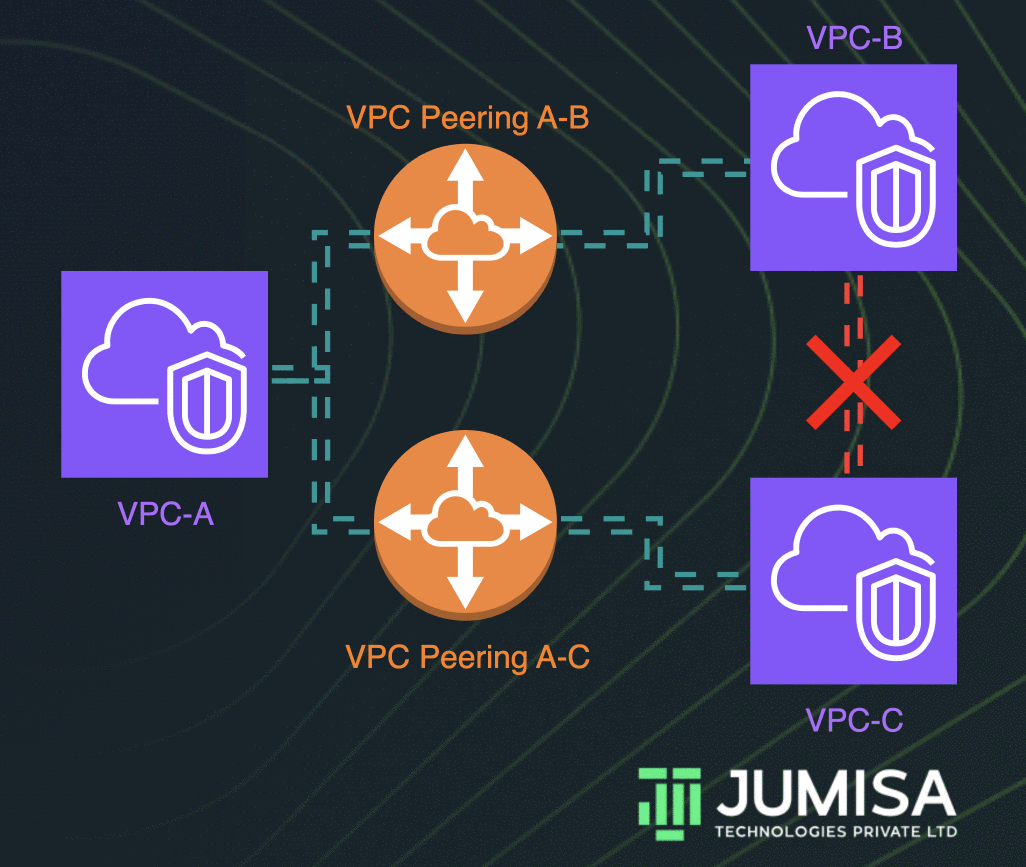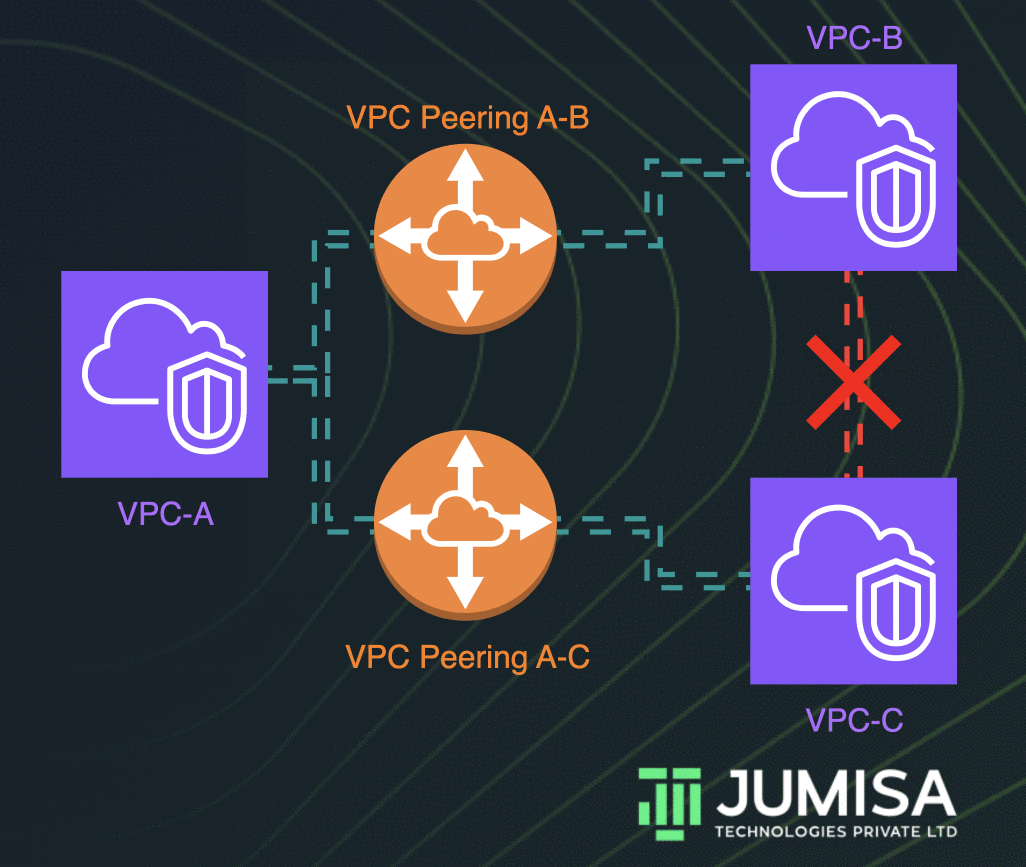
RemoteIoT VPC refers to a specialized virtual private cloud (VPC) architecture designed explicitly for managing remote IoT devices and networks. It serves as a secure and isolated environment where IoT devices can communicate and exchange data without exposing sensitive information to public networks. By leveraging RemoteIoT VPC, organizations can enhance the security, scalability, and efficiency of their IoT deployments.
In a RemoteIoT VPC setup, resources are logically isolated from other networks, ensuring that only authorized devices and users can access the network. This isolation is critical for maintaining data integrity and protecting against cyber threats. Additionally, RemoteIoT VPC provides flexibility in configuring network settings, allowing administrators to tailor the environment to meet specific operational requirements.
How Does RemoteIoT VPC Work?
The functioning of RemoteIoT VPC revolves around creating a private network space within a public cloud infrastructure. This is achieved through the use of subnets, access control lists (ACLs), and security groups, which collectively define the rules governing network traffic. Devices connected to the RemoteIoT VPC can communicate securely with each other and with external systems, provided they adhere to the predefined security protocols.
Key features:
- Isolated network environment for IoT devices
- Flexible configuration options for network settings
- Enhanced security through access controls and encryption
- Scalability to accommodate growing numbers of devices
Importance of VPC for IoT
The Internet of Things (IoT) presents unique challenges when it comes to network security and management. Traditional network architectures often fall short in addressing these challenges, making the use of VPCs essential for IoT deployments. RemoteIoT VPC addresses these concerns by providing a secure and scalable environment tailored to the needs of IoT applications.
One of the primary advantages of using a VPC for IoT is the ability to isolate IoT devices from other network resources. This isolation helps prevent unauthorized access and reduces the risk of data breaches. Furthermore, VPCs enable fine-grained control over network traffic, allowing administrators to define precise rules for device communication and data exchange.
Why Choose RemoteIoT VPC Over Traditional Networks?
Compared to traditional networks, RemoteIoT VPC offers several advantages that make it an ideal choice for IoT deployments:
- Enhanced security through isolation and access controls
- Improved scalability to handle large numbers of devices
- Greater flexibility in configuring network settings
- Reduced operational costs through efficient resource management
Key Components of RemoteIoT VPC
Understanding the key components of RemoteIoT VPC is essential for effectively designing and managing IoT networks. These components work together to create a secure and efficient environment for IoT devices.
Subnets
Subnets divide the RemoteIoT VPC into smaller network segments, each with its own IP address range. This segmentation enhances security by isolating devices with different roles or security requirements.
Security Groups
Security groups act as virtual firewalls, controlling inbound and outbound traffic to and from devices within the RemoteIoT VPC. Administrators can define rules to specify which types of traffic are allowed or denied.
Access Control Lists (ACLs)
ACLs provide an additional layer of security by controlling traffic at the subnet level. They define which IP addresses are allowed to communicate with devices in a particular subnet.
Benefits of Using RemoteIoT VPC
Adopting RemoteIoT VPC brings numerous benefits that can significantly enhance the performance and security of IoT deployments. These benefits include:
- Enhanced Security: Isolation of IoT devices from other networks reduces the risk of unauthorized access and data breaches.
- Improved Scalability: RemoteIoT VPC can easily accommodate growing numbers of devices, ensuring that the network remains efficient as it expands.
- Cost Efficiency: By optimizing resource usage and reducing the need for additional hardware, RemoteIoT VPC helps lower operational costs.
- Flexibility: Administrators can configure network settings to meet specific operational requirements, ensuring optimal performance for IoT applications.
Security Features of RemoteIoT VPC
Security is a top priority in IoT deployments, and RemoteIoT VPC offers a range of features to safeguard against cyber threats. These features include encryption, access controls, and monitoring tools that help protect data and maintain network integrity.
Encryption
Data transmitted within a RemoteIoT VPC is encrypted to prevent unauthorized access. This ensures that sensitive information remains secure even if intercepted during transmission.
Monitoring and Alerts
RemoteIoT VPC provides monitoring tools that allow administrators to track network activity and receive alerts in case of suspicious behavior. This proactive approach helps detect and mitigate potential security threats before they can cause damage.
Deployment Strategies for RemoteIoT VPC
Successfully deploying RemoteIoT VPC requires careful planning and execution. Below are some strategies to consider when implementing this architecture:
- Define Network Requirements: Identify the specific needs of your IoT deployment, such as the number of devices and required bandwidth.
- Configure Security Settings: Set up security groups and ACLs to control access to devices and data.
- Test and Validate: Conduct thorough testing to ensure that the RemoteIoT VPC functions as intended before going live.
Scaling and Management
As IoT deployments grow, the ability to scale and manage networks becomes increasingly important. RemoteIoT VPC offers tools and features that simplify the process of scaling and managing large-scale IoT networks.
Automation Tools
Automation tools can streamline the management of RemoteIoT VPC by automating routine tasks such as device provisioning and configuration updates. This reduces the workload on administrators and minimizes the risk of human error.
Monitoring and Reporting
Comprehensive monitoring and reporting capabilities enable administrators to track network performance and identify areas for improvement. These insights help optimize resource usage and ensure that the network remains efficient and secure.
Common Challenges and Solutions
While RemoteIoT VPC offers many advantages, there are also challenges to consider. Below are some common challenges and their solutions:
- Challenge: Complexity of setup and configuration
- Solution: Utilize documentation and support resources to simplify the process
- Challenge: Ensuring consistent security across devices
- Solution: Implement standardized security protocols and regularly update them
Real-World Applications of RemoteIoT VPC
RemoteIoT VPC has been successfully implemented in various industries, demonstrating its versatility and effectiveness. Some notable applications include:
- Smart Cities: Managing large-scale IoT networks for urban infrastructure
- Healthcare: Securing medical devices and protecting patient data
- Manufacturing: Optimizing production processes through IoT integration
Future Trends in RemoteIoT VPC
The future of RemoteIoT VPC looks promising, with advancements in technology driving innovation in IoT network architecture. Key trends to watch include:
- Integration with AI and Machine Learning: Enhancing network management through intelligent automation
- Edge Computing: Improving data processing speeds by bringing computation closer to the source
- 5G Connectivity: Enabling faster and more reliable communication between devices
Conclusion
RemoteIoT VPC represents a significant advancement in IoT network architecture, offering a secure and scalable solution for managing remote IoT devices. By understanding its key components, benefits, and deployment strategies, organizations can harness the full potential of this technology to drive innovation and growth.
We encourage you to explore the possibilities of RemoteIoT VPC further and consider implementing it in your IoT deployments. Feel free to leave a comment or share this article with others who may find it valuable. For more insights into IoT and related technologies, be sure to check out our other articles on the subject.