Securing your RPi3 VNC server is an essential task for anyone who uses Raspberry Pi 3 as a remote workstation. With the increasing number of cyber threats targeting IoT devices, ensuring the safety of your setup is no longer optional. Whether you're a hobbyist or a professional, securing your VNC server will protect sensitive data and prevent unauthorized access.
Remote desktop access has revolutionized the way we work and manage systems. The Raspberry Pi 3, combined with a VNC server, allows users to access their desktop environment remotely, making it an ideal solution for lightweight tasks. However, this convenience comes with risks, as leaving your VNC server unprotected can expose it to malicious actors.
In this article, we will delve into the best practices for securing your RPi3 VNC server, ensuring it remains safe from potential threats. From configuring firewalls to implementing encryption protocols, this guide will cover everything you need to know to protect your setup effectively.
Table of Contents
- Introduction to VNC
- Understanding Security Risks
- Biometric Authentication
- Firewall Configuration
- Encryption Methods
- User Access Management
- Regular Updates
- Network Segregation
- Logging and Monitoring
- Best Practices for Security
Introduction to VNC
Virtual Network Computing (VNC) is a graphical desktop sharing system that allows users to remotely control another computer. For Raspberry Pi 3 users, setting up a VNC server enables seamless remote access to the device's desktop environment. However, the default configuration of VNC may not be secure enough for real-world use.
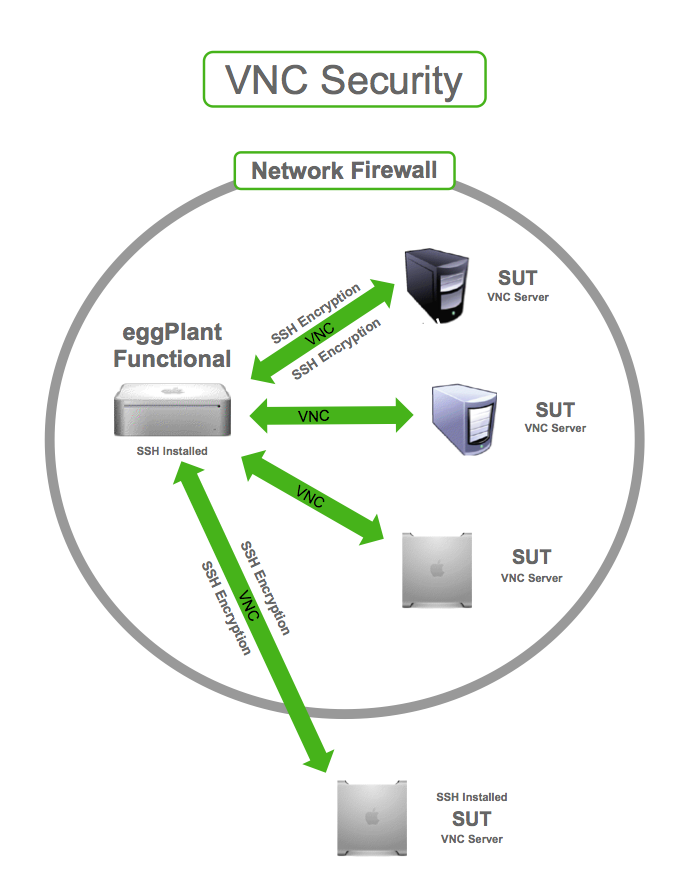
To enhance security, it is crucial to understand the architecture of VNC and how it operates. VNC works by sending keyboard and mouse input from the client to the server and returning screen updates to the client. This process can be intercepted if proper security measures are not implemented.
Why Choose VNC for RPi3?
- Lightweight and easy to set up
- Compatible with multiple operating systems
- Supports high-resolution displays
Understanding Security Risks
Securing your RPi3 VNC server starts with understanding the potential risks involved. Without proper protection, your device could become a target for malicious activities such as unauthorized access, data breaches, and malware infections. Below are some common security risks associated with VNC servers:
- Brute Force Attacks: Automated scripts can attempt to guess your VNC password repeatedly until they gain access.
- Man-in-the-Middle Attacks: Without encryption, attackers can intercept and manipulate data transmitted between the client and server.
- Outdated Software: Running outdated VNC server software increases the risk of vulnerabilities being exploited.
Common Attack Vectors
Attackers often exploit weak passwords, unpatched software, and misconfigured firewalls to gain unauthorized access. By staying informed about these risks, you can take proactive steps to secure your RPi3 VNC server.
Biometric Authentication
One of the most effective ways to enhance security is by implementing biometric authentication. Although biometric solutions are not natively supported by VNC, you can integrate them using third-party tools and services. Biometric authentication adds an extra layer of security by requiring physical characteristics, such as fingerprints or facial recognition, to verify user identity.
Advantages of Biometric Authentication
- Reduces reliance on passwords
- Minimizes the risk of unauthorized access
- Improves user convenience
Firewall Configuration
Configuring a firewall is a fundamental step in securing your RPi3 VNC server. A firewall acts as a barrier between your device and the outside world, controlling incoming and outgoing network traffic. By setting up a firewall, you can restrict access to your VNC server, ensuring only authorized devices can connect.
Steps to Configure a Firewall
- Install a firewall management tool like UFW (Uncomplicated Firewall).
- Allow only necessary ports, such as port 5900 for VNC.
- Deny all other incoming connections to minimize exposure.
Encryption Methods
Encrypting data transmitted between the VNC client and server is essential for maintaining privacy and security. Encryption ensures that even if an attacker intercepts the data, they will not be able to decipher it without the encryption key. Popular encryption methods for VNC include SSL/TLS and AES.
Implementing Encryption in VNC
To enable encryption in your VNC setup, consider using a secure VNC client that supports encrypted connections. Additionally, you can configure your VNC server to require encryption for all connections.
User Access Management
Managing user access is critical for maintaining the security of your RPi3 VNC server. By implementing role-based access control (RBAC), you can define specific permissions for each user, ensuring they only have access to the resources they need.
Best Practices for User Access Management
- Create separate user accounts for each individual accessing the server.
- Assign appropriate permissions based on the user's role.
- Regularly review and update user access privileges.
Regular Updates
Keeping your software up to date is one of the simplest yet most effective ways to secure your RPi3 VNC server. Regular updates ensure that any known vulnerabilities are patched, reducing the risk of exploitation. Additionally, updates often include performance improvements and new features that can enhance your overall experience.
How to Stay Updated
To keep your RPi3 VNC server updated, follow these steps:
- Enable automatic updates for your operating system and VNC server software.
- Regularly check for updates manually to ensure nothing is missed.
- Subscribe to security bulletins from trusted sources to stay informed about potential threats.
Network Segregation
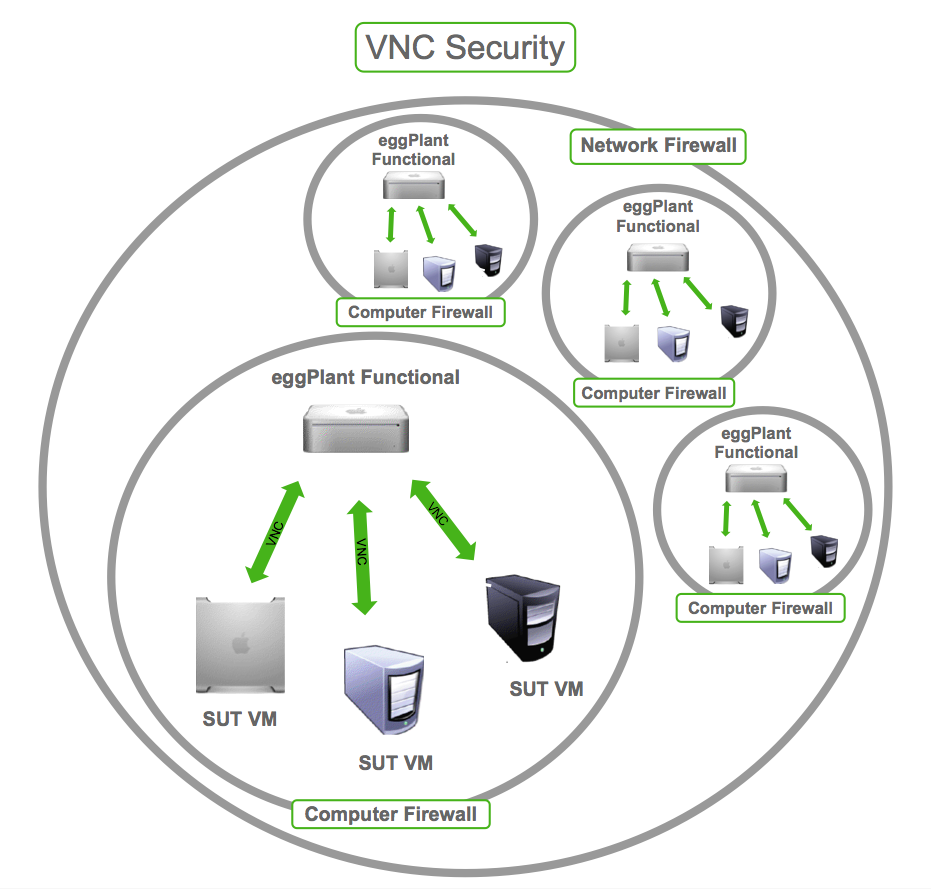
Segregating your network is another effective strategy for enhancing security. By isolating your RPi3 VNC server from other devices on your network, you can limit the potential impact of a security breach. Network segregation can be achieved using VLANs, subnets, or dedicated network segments.
Benefits of Network Segregation
- Reduces the attack surface for potential threats.
- Improves overall network performance.
- Facilitates easier monitoring and management.
Logging and Monitoring
Implementing logging and monitoring solutions is crucial for detecting and responding to security incidents. By tracking access attempts and system activities, you can identify suspicious behavior and take corrective actions promptly. Tools like fail2ban and logwatch can help automate this process.
Setting Up Logging and Monitoring
- Enable logging for your VNC server and firewall.
- Set up alerts for unusual activity, such as repeated failed login attempts.
- Regularly review logs to identify potential security issues.
Best Practices for Security
To ensure the highest level of security for your RPi3 VNC server, follow these best practices:
- Use strong, unique passwords for all user accounts.
- Enable two-factor authentication (2FA) whenever possible.
- Limit the number of failed login attempts allowed.
- Regularly back up important data to prevent loss in case of a breach.
Final Thoughts
Securing your RPi3 VNC server requires a combination of technical expertise and vigilance. By following the guidelines outlined in this article, you can significantly reduce the risk of cyber threats and protect your data from unauthorized access. Remember, security is an ongoing process, and staying informed about emerging threats is key to maintaining a secure setup.
Conclusion
In conclusion, securing your RPi3 VNC server is a critical task that should not be overlooked. By implementing the strategies discussed in this article, such as configuring firewalls, enabling encryption, and managing user access, you can create a robust security framework for your setup. We encourage you to take action today and ensure your RPi3 VNC server remains safe from potential threats.
Feel free to share your thoughts and experiences in the comments section below. Additionally, explore our other articles for more tips and insights on securing your IoT devices. Together, let's build a safer digital environment!