In the era of interconnected devices, free remote login IoT device solutions have become increasingly important for businesses and individuals alike. The ability to access IoT devices remotely not only enhances convenience but also improves efficiency and productivity. However, ensuring security and reliability remains a top priority when selecting a remote access solution.
As the Internet of Things (IoT) continues to grow, more devices are being connected to the internet, creating opportunities for automation and data collection. Remote login capabilities allow users to manage and monitor these devices from anywhere in the world. This guide will explore the best practices, tools, and strategies for implementing secure remote login solutions for IoT devices.
Whether you're a business owner, IT professional, or tech enthusiast, understanding how to implement a free remote login IoT device system is essential. In this article, we'll cover everything you need to know about remote access solutions, including security considerations, setup processes, and troubleshooting tips.
Table of Contents
- What is Remote Login IoT?
- Benefits of Remote Login IoT Devices
- Security Considerations for Free Remote Login IoT Device
- Tools and Software for Remote Login IoT
- Setup Process for Free Remote Login IoT Device
- Troubleshooting Tips for Remote Login IoT Devices
- Best Practices for Secure Remote Login IoT Device
- Cost-Effective Solutions for Remote Login IoT
- Future Trends in Remote Login IoT Technology
- Conclusion
What is Remote Login IoT?
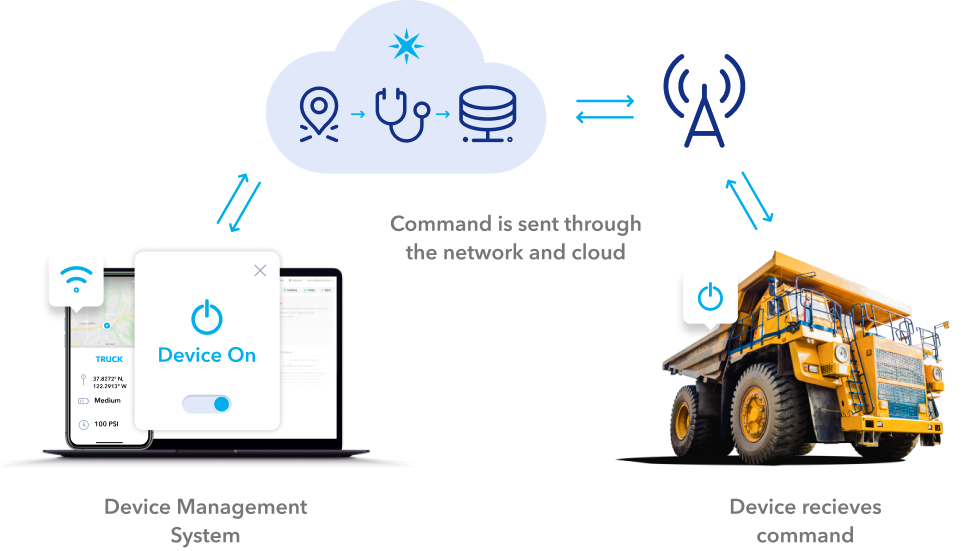
Remote login IoT refers to the ability to access and control IoT devices over the internet from a remote location. This technology allows users to monitor, manage, and interact with connected devices without being physically present. Remote login IoT solutions are widely used in industries such as manufacturing, healthcare, agriculture, and smart homes.
By leveraging remote login capabilities, businesses can improve operational efficiency, reduce downtime, and enhance customer service. For example, a technician can diagnose and resolve issues with a remote device without needing to visit the site in person.
How Does Remote Login IoT Work?
The process of remote login IoT typically involves the following steps:
- Device connection to the internet
- Authentication and authorization
- Secure communication channel establishment
- Remote access and control
Modern remote login solutions often use protocols such as SSH (Secure Shell), RDP (Remote Desktop Protocol), or proprietary APIs to facilitate secure communication between the user and the IoT device.
Benefits of Remote Login IoT Devices
Implementing a free remote login IoT device system offers numerous advantages for businesses and individuals. Some of the key benefits include:
- Improved efficiency through remote monitoring and control
- Reduced operational costs by minimizing the need for on-site visits
- Enhanced security through centralized management and monitoring
- Increased flexibility and convenience for users
- Real-time data access and analysis
These benefits make remote login IoT solutions an attractive option for organizations looking to streamline their operations and improve service delivery.
Security Considerations for Free Remote Login IoT Device
Security is a critical aspect of any remote login IoT implementation. Without proper security measures, IoT devices can become vulnerable to cyberattacks, leading to data breaches, unauthorized access, and other security risks. Below are some important security considerations for free remote login IoT devices:
- Use strong authentication methods, such as two-factor authentication (2FA)
- Encrypt all communication channels using protocols like SSL/TLS
- Regularly update firmware and software to address security vulnerabilities
- Implement firewalls and intrusion detection systems
- Limit access to authorized users only
By following these best practices, you can significantly reduce the risk of security breaches and ensure the safety of your IoT devices.
Common Security Threats in Remote Login IoT
Some of the most common security threats associated with remote login IoT devices include:
- Brute force attacks
- Man-in-the-middle (MITM) attacks
- Malware infections
- Denial-of-service (DoS) attacks
Understanding these threats and taking proactive measures to mitigate them is essential for maintaining the security of your IoT infrastructure.
Tools and Software for Remote Login IoT
There are several tools and software solutions available for implementing free remote login IoT device systems. These tools range from open-source platforms to commercial solutions, each offering unique features and capabilities. Some of the most popular options include:
- TeamViewer
- AnyDesk
- SecureCRT
- Putty
- Windows Remote Desktop
When selecting a tool or software for your remote login IoT needs, consider factors such as ease of use, security features, compatibility, and cost.
Open-Source vs. Commercial Solutions
Open-source solutions for remote login IoT devices, such as SSH and Putty, offer flexibility and cost savings but may require more technical expertise to set up and maintain. On the other hand, commercial solutions like TeamViewer and AnyDesk provide user-friendly interfaces and robust security features, often at a higher cost.
Setup Process for Free Remote Login IoT Device
Setting up a free remote login IoT device system involves several steps, including device configuration, network setup, and security implementation. Below is a step-by-step guide to help you get started:
- Connect your IoT device to the internet
- Install and configure the remote login software on both the device and the client machine
- Set up authentication and authorization mechanisms
- Establish a secure communication channel
- Test the connection and ensure proper functionality
Following these steps will help ensure a smooth and secure setup process for your remote login IoT device system.
Troubleshooting Common Issues
During the setup process, you may encounter various issues that can hinder the successful implementation of your remote login IoT system. Some common problems and their solutions include:
- Connection issues: Verify network settings and ensure proper device configuration
- Authentication failures: Double-check username and password credentials
- Slow performance: Optimize network bandwidth and reduce unnecessary traffic
Troubleshooting Tips for Remote Login IoT Devices
Effective troubleshooting is essential for maintaining the reliability and performance of your remote login IoT device system. Below are some tips to help you diagnose and resolve common issues:
- Check device logs for error messages and diagnostic information
- Restart the device and client machine to clear temporary issues
- Update firmware and software to the latest versions
- Consult the user manual or online documentation for guidance
By following these troubleshooting tips, you can quickly identify and resolve issues, ensuring smooth operation of your remote login IoT system.
Best Practices for Secure Remote Login IoT Device
To ensure the security and reliability of your free remote login IoT device system, it's important to follow best practices. Some key recommendations include:
- Use strong, unique passwords for all devices and accounts
- Regularly back up important data and configurations
- Monitor system activity for suspicious behavior
- Limit access to trusted users and devices only
Implementing these best practices will help protect your IoT infrastructure from potential threats and ensure long-term success.
Regular Maintenance and Updates
Regular maintenance and updates are crucial for maintaining the security and functionality of your remote login IoT system. Schedule routine checks to verify device performance, update software, and address any security vulnerabilities.
Cost-Effective Solutions for Remote Login IoT
While commercial remote login IoT solutions can be expensive, there are several cost-effective alternatives available. Open-source platforms like SSH and Putty offer free remote login capabilities with robust security features. Additionally, cloud-based solutions like AWS IoT Core and Google Cloud IoT provide scalable and affordable options for managing IoT devices remotely.
When evaluating cost-effective solutions, consider factors such as scalability, ease of use, and long-term maintenance costs to ensure the best value for your investment.
Future Trends in Remote Login IoT Technology
The field of remote login IoT technology is rapidly evolving, with new innovations and advancements emerging regularly. Some of the key trends to watch in the coming years include:
- Increased adoption of edge computing for faster data processing
- Integration of artificial intelligence (AI) and machine learning (ML) for predictive maintenance
- Enhanced security measures, such as quantum cryptography
- Greater emphasis on interoperability and standardization
Staying informed about these trends will help you prepare for the future of remote login IoT technology and make informed decisions for your organization.
Conclusion
Free remote login IoT device solutions offer numerous benefits for businesses and individuals, including improved efficiency, reduced costs, and enhanced security. By following best practices and implementing secure remote login systems, you can take full advantage of the opportunities provided by IoT technology.
We encourage you to share your thoughts and experiences with remote login IoT devices in the comments section below. Additionally, feel free to explore other articles on our website for more insights into the world of IoT and technology.