In today's fast-paced digital landscape, AWS IoT remote access has become a game-changer for businesses looking to enhance connectivity and automation. This technology bridges the gap between devices and cloud infrastructure, enabling seamless interaction and data exchange. With AWS IoT remote access, companies can unlock new possibilities in remote monitoring, device management, and real-time analytics.
As industries continue to embrace the Internet of Things (IoT), the need for secure and efficient remote access solutions has never been more critical. AWS IoT offers a robust platform that simplifies the process of connecting devices to the cloud, ensuring scalability and reliability. Whether it's manufacturing plants, smart homes, or healthcare facilities, the applications of AWS IoT remote access are virtually limitless.
In this comprehensive guide, we will explore the ins and outs of AWS IoT remote access. From understanding its core functionalities to implementing best practices, this article aims to equip you with the knowledge needed to harness the full potential of this cutting-edge technology. Let's dive in!
Table of Contents
- Introduction to AWS IoT Remote Access
- AWS IoT Remote Access Architecture
- Benefits of Using AWS IoT Remote Access
- How to Implement AWS IoT Remote Access
- Security Features of AWS IoT Remote Access
- Real-World Use Cases of AWS IoT Remote Access
- AWS IoT Remote Access vs. Other Solutions
- Optimizing AWS IoT Remote Access Performance
- Troubleshooting Common Issues
- The Future of AWS IoT Remote Access
Introduction to AWS IoT Remote Access
Understanding AWS IoT
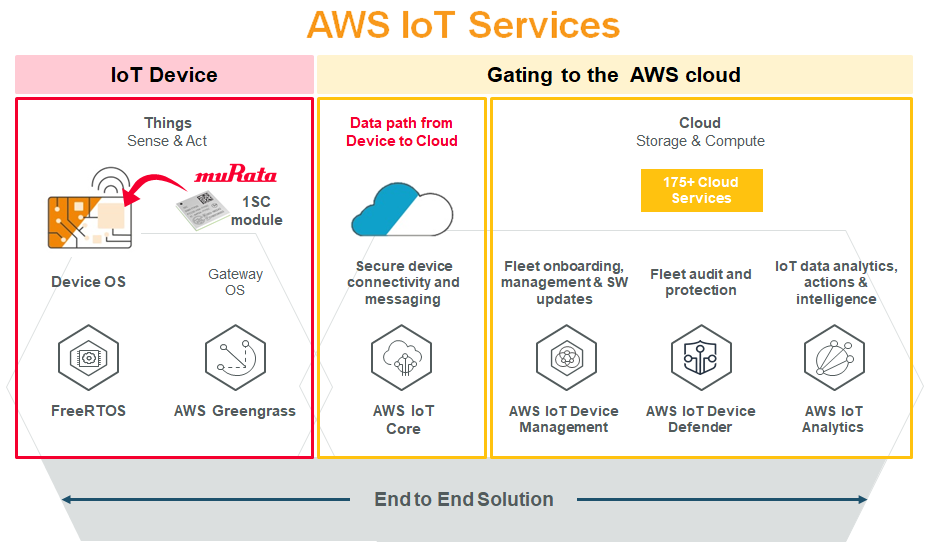
AWS IoT is a managed cloud platform designed to connect devices to the AWS cloud and other devices securely and reliably. It enables devices to easily interact with cloud applications and other devices. AWS IoT remote access is a key component of this ecosystem, allowing businesses to manage and monitor devices remotely.
Core Features of AWS IoT Remote Access
Some of the standout features of AWS IoT remote access include secure device connections, message routing, and data processing. These capabilities are supported by a range of services such as AWS IoT Core, AWS IoT Device Management, and AWS IoT Greengrass.
- Secure Device Connections
- Message Routing
- Data Processing
AWS IoT Remote Access Architecture
Key Components of the Architecture
The architecture of AWS IoT remote access revolves around several key components:
- AWS IoT Core: Handles secure communication between devices and the cloud.
- AWS IoT Device Management: Provides tools for device provisioning, monitoring, and updates.
- AWS IoT Greengrass: Extends AWS to edge devices for local computing, messaging, and data caching.
How the Components Work Together
These components work in tandem to create a seamless experience for managing IoT devices remotely. For instance, AWS IoT Core ensures secure communication, while AWS IoT Device Management simplifies the process of maintaining devices at scale.
Benefits of Using AWS IoT Remote Access
AWS IoT remote access offers numerous advantages for businesses looking to leverage IoT technology. Some of these benefits include:
- Scalability: Easily scale your IoT infrastructure to accommodate growing needs.
- Security: Robust security features protect your devices and data from unauthorized access.
- Cost Efficiency: Reduce costs associated with on-premises infrastructure by leveraging cloud-based solutions.
How to Implement AWS IoT Remote Access
Step-by-Step Guide
Implementing AWS IoT remote access involves several steps:
- Set Up AWS IoT Core: Configure AWS IoT Core to handle device communication.
- Provision Devices: Use AWS IoT Device Management to provision and register devices.
- Develop Applications: Build applications that interact with devices through AWS IoT Core.
Best Practices for Implementation
To ensure successful implementation, follow these best practices:
- Plan your architecture carefully to optimize performance.
- Regularly update devices to address security vulnerabilities.
- Monitor device performance and usage to identify potential issues.
Security Features of AWS IoT Remote Access
Encryption and Authentication
AWS IoT remote access employs advanced encryption and authentication mechanisms to safeguard data. Devices communicate securely using Transport Layer Security (TLS), ensuring that only authorized devices can access the network.
Device Security Policies
Implementing strict device security policies is crucial for maintaining the integrity of your IoT ecosystem. AWS IoT provides tools to enforce these policies, such as device-specific permissions and access controls.
Real-World Use Cases of AWS IoT Remote Access
Smart Manufacturing
In the manufacturing sector, AWS IoT remote access enables real-time monitoring of production lines, reducing downtime and improving efficiency. Companies can remotely manage equipment and receive alerts for maintenance needs.
Remote Healthcare
Healthcare providers leverage AWS IoT remote access to monitor patients' health conditions in real time. This allows for timely interventions and improved patient outcomes.
AWS IoT Remote Access vs. Other Solutions
Comparing AWS IoT with Competitors
When compared to other IoT platforms, AWS IoT remote access stands out due to its scalability, security, and integration capabilities. While competitors like Microsoft Azure IoT and Google Cloud IoT offer similar features, AWS IoT's extensive ecosystem and global presence make it a top choice for businesses.
Why Choose AWS IoT?
Key reasons to choose AWS IoT remote access include:
- Comprehensive suite of services.
- Strong focus on security and compliance.
- Wide range of integration options with other AWS services.
Optimizing AWS IoT Remote Access Performance
Tips for Optimization
Optimizing the performance of AWS IoT remote access involves:
- Monitoring device performance regularly.
- Using AWS CloudWatch to track metrics and logs.
- Implementing caching strategies to reduce latency.
Advanced Techniques
For advanced optimization, consider leveraging machine learning models to predict device behavior and automate responses. AWS IoT Analytics can help analyze large datasets to uncover insights and improve decision-making.
Troubleshooting Common Issues
Identifying and Resolving Problems
Common issues with AWS IoT remote access include connectivity problems and security breaches. To troubleshoot these issues:
- Check device configurations for errors.
- Review security policies and permissions.
- Consult AWS documentation and support resources.
Best Practices for Troubleshooting
Adopting best practices for troubleshooting can save time and effort:
- Document all issues and resolutions for future reference.
- Collaborate with your team to identify root causes.
- Stay updated on AWS IoT developments and updates.
The Future of AWS IoT Remote Access
As technology continues to evolve, the future of AWS IoT remote access looks promising. AWS is committed to enhancing its IoT offerings by incorporating emerging technologies such as 5G, edge computing, and artificial intelligence. These advancements will further expand the capabilities of AWS IoT remote access, making it an indispensable tool for businesses worldwide.
Conclusion
AWS IoT remote access represents a significant leap forward in the world of IoT technology. By providing scalable, secure, and cost-effective solutions, it empowers businesses to unlock new opportunities and drive innovation. From smart manufacturing to remote healthcare, the applications of AWS IoT remote access are vast and varied.
We encourage you to explore the possibilities offered by AWS IoT remote access and take the first step toward transforming your business. Share your thoughts and experiences in the comments below, and don't forget to check out our other articles for more insights into cutting-edge technologies.
References:
- AWS Documentation - https://docs.aws.amazon.com
- AWS IoT Blog - https://aws.amazon.com/blogs/iot/
- Gartner IoT Report - https://www.gartner.com/en