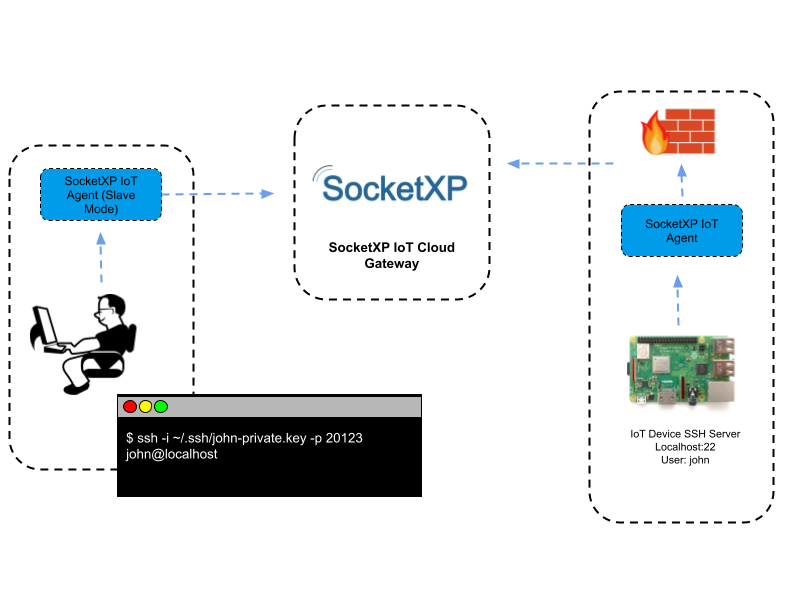
In today's interconnected world, remote access to devices like the Raspberry Pi has become an essential skill for hobbyists, developers, and professionals alike. The ability to securely connect to your Raspberry Pi from anywhere offers unparalleled convenience and flexibility. However, ensuring that this connection is secure is crucial to protect your data and privacy.
Remote access to Raspberry Pi allows users to control their devices from remote locations, making it a powerful tool for managing servers, IoT projects, or home automation systems. Whether you're a beginner or an advanced user, understanding how to set up and maintain secure remote access is vital.
This article will guide you through the process of setting up secure remote access to your Raspberry Pi, addressing common concerns, offering best practices, and providing actionable tips. By the end, you'll have the knowledge and tools necessary to establish a secure and efficient remote connection.
Table of Contents
- Introduction to Secure Remote Access
- Why Secure Remote Access is Important
- Preparation Before Setting Up
- Setting Up SSH on Raspberry Pi
- Setting Up VNC for Remote Desktop Access
- Configuring Network Settings
- Securing Your Raspberry Pi with Firewall
- Advanced Security Measures
- Troubleshooting Common Issues
- Best Practices for Secure Remote Access
- Conclusion and Next Steps
Introduction to Secure Remote Access
Secure remote access to Raspberry Pi enables users to interact with their devices from anywhere in the world. This functionality is particularly useful for managing headless setups, monitoring IoT devices, or accessing files remotely. However, with great power comes great responsibility. Ensuring that your remote connections are secure is critical to avoid unauthorized access and potential data breaches.
The most common methods for remote access include SSH (Secure Shell) and VNC (Virtual Network Computing). Both methods offer unique advantages and can be configured to meet your specific needs. Understanding the basics of these technologies is the first step toward setting up a secure remote connection.
Why Secure Remote Access is Important
When discussing how to use secure remote access to Raspberry Pi, it's essential to emphasize the importance of security. Without proper protection, your Raspberry Pi could become vulnerable to cyber threats such as hacking, malware, or unauthorized access.
Here are some reasons why secure remote access is crucial:
- Protects sensitive data stored on your Raspberry Pi.
- Prevents unauthorized users from gaining control of your device.
- Ensures the integrity of your IoT projects or home automation systems.
- Reduces the risk of cyberattacks that could compromise your network.
Preparation Before Setting Up
Before diving into the technical aspects of setting up secure remote access, it's important to prepare your Raspberry Pi and ensure it's ready for the process. This section will cover the necessary steps to prepare your device.
Checking System Requirements
Ensure that your Raspberry Pi meets the following requirements:
- Running the latest version of Raspberry Pi OS.
- Connected to a stable internet connection.
- Up-to-date with the latest security patches and updates.
Updating Your Raspberry Pi
Run the following commands to update your Raspberry Pi:
sudo apt update && sudo apt upgrade
Setting Up SSH on Raspberry Pi
SSH (Secure Shell) is one of the most popular methods for remote access due to its simplicity and security. It allows users to connect to their Raspberry Pi via a terminal interface, making it ideal for command-line tasks.
Enabling SSH
To enable SSH on your Raspberry Pi, follow these steps:
- Open the Raspberry Pi Configuration tool by typing
sudo raspi-configin the terminal. - Select "Interfacing Options" and navigate to "SSH."
- Choose "Yes" to enable SSH and confirm your choice.
Connecting via SSH
Once SSH is enabled, you can connect to your Raspberry Pi using an SSH client such as PuTTY (for Windows) or the built-in terminal on macOS and Linux. Use the following format to connect:
ssh pi@your_raspberry_pi_ip_address
Setting Up VNC for Remote Desktop Access
While SSH is ideal for command-line tasks, VNC (Virtual Network Computing) provides a graphical interface for remote access. This method is perfect for users who prefer a desktop-like experience when working with their Raspberry Pi.
Installing VNC Server
To install VNC Server on your Raspberry Pi, follow these steps:
- Open the terminal and type
sudo apt install realvnc-vnc-server realvnc-vnc-viewer. - Follow the prompts to complete the installation.
Connecting via VNC
Once VNC Server is installed, you can connect to your Raspberry Pi using a VNC Viewer application. Enter your Raspberry Pi's IP address and login credentials to establish the connection.
Configuring Network Settings
Proper network configuration is essential for ensuring that your Raspberry Pi can be accessed remotely. This section will guide you through the necessary steps to configure your network settings.
Assigning a Static IP Address
Assigning a static IP address to your Raspberry Pi ensures that its address remains consistent, making it easier to connect remotely. Follow these steps:
- Edit the dhcpcd configuration file:
sudo nano /etc/dhcpcd.conf. - Add the following lines to assign a static IP address:
- Restart the networking service:
sudo service dhcpcd restart.
Securing Your Raspberry Pi with Firewall
Implementing a firewall is a crucial step in securing your Raspberry Pi. A firewall helps protect your device by controlling incoming and outgoing network traffic based on predefined rules.
Installing UFW
UFW (Uncomplicated Firewall) is a user-friendly firewall management tool for Linux. To install UFW on your Raspberry Pi, run the following command:
sudo apt install ufw
Configuring UFW Rules
Set up UFW rules to allow SSH and VNC connections while blocking unnecessary traffic:
- Allow SSH:
sudo ufw allow 22. - Allow VNC:
sudo ufw allow 5900. - Enable UFW:
sudo ufw enable.
Advanced Security Measures
In addition to basic security measures, implementing advanced techniques can further enhance the security of your Raspberry Pi. Consider the following strategies:
Using Strong Passwords
Create strong, unique passwords for your Raspberry Pi accounts. Avoid using easily guessable passwords and enable two-factor authentication whenever possible.
Disabling Root Login
Disabling root login via SSH reduces the risk of unauthorized access. Edit the SSH configuration file (/etc/ssh/sshd_config) and set PermitRootLogin no.
Troubleshooting Common Issues
Despite following the steps carefully, you may encounter issues when setting up secure remote access to your Raspberry Pi. This section addresses common problems and provides solutions.
Unable to Connect via SSH
If you're unable to connect via SSH, check the following:
- Ensure that SSH is enabled on your Raspberry Pi.
- Verify that your Raspberry Pi's IP address is correct.
- Check your firewall settings to ensure that port 22 is open.
Best Practices for Secure Remote Access
To ensure the highest level of security when using remote access to your Raspberry Pi, follow these best practices:
- Regularly update your Raspberry Pi's software and firmware.
- Use strong, unique passwords and enable two-factor authentication.
- Limit SSH access to trusted IP addresses whenever possible.
- Monitor your Raspberry Pi's logs for suspicious activity.
Conclusion and Next Steps
In conclusion, setting up secure remote access to your Raspberry Pi is a valuable skill that offers numerous benefits. By following the steps outlined in this article, you can establish a secure and efficient connection to your device from anywhere in the world. Remember to prioritize security and adhere to best practices to protect your data and privacy.
We encourage you to share your thoughts and experiences in the comments section below. If you found this article helpful, consider sharing it with others who might benefit from the information. Additionally, explore our other articles for more tips and tutorials on Raspberry Pi and related technologies.